User Management
Users on the platform have a role and can have special permissions to manage their access level.
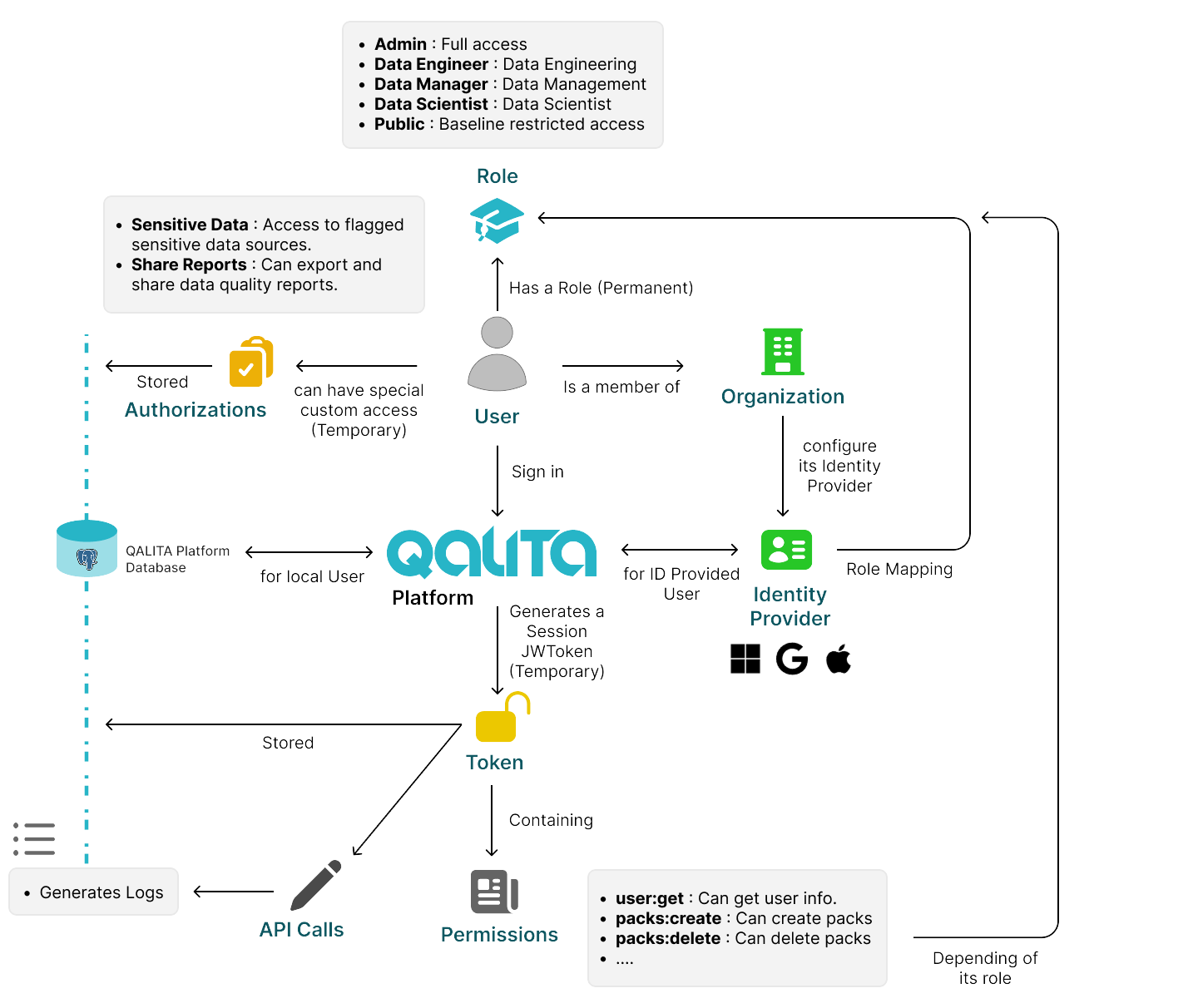
Overall graph on permission and user management
Authentication Modes
QALITA Platform supports the following authentication modes : local, LDAP, OIDC SAML.
By default, any user is assigned the public role on their first login, unless a role mapping is specified in the LDAP configuration.
Local Users
Sign Up
With authentication in table mode, users can directly [Sign Up] from the home page of Platform.
As Admin, Create a User
As administrator, you can also create a local user, go to the Users & Roles section in the Settings menu.
LDAP Registry
Users can authenticate with a password and email. This authentication can be configured to work with a corporate directory using the LDAP protocol.
Configure LDAP
To configure LDAP authentication, you need to add environment variables to the Backend.
LDAP_SERVER: LDAP server addressldap://openldap:389LDAP_DN: Base DN for user searchdc=example,dc=orgLDAP_TLS: Enable TLSfalseLDAP_SEARCH_USER: Search usercn=admin,dc=example,dc=orgLDAP_SEARCH_PASSWORD: Search user passwordadminpasswordLDAP_SEARCH_USER_FILTER: User search filter(&(objectClass=person)(uid=%s))LDAP_SEARCH_GROUP_FILTER: Group search filter(&(objectClass=posixGroup)(memberUid=%s))LDAP_ROLE_MAPPING: Role mappingadmin:cn=direction,dc=qalita,dc=io;dataengineer:cn=factory,dc=qalita,dc=io;datamanager:cn=conseil,dc=qalita,dc=io
Microsoft Authentication (OIDC/SAML)
Users can authenticate with Microsoft Entra ID.
Configure Microsoft (Azure Entra) OIDC
To configure Microsoft (OIDC) authentication, you need to add environment variables to the Backend.
QALITA_AUTH_MODE: Specify the authentication modesamlMICROSOFT_CLIENT_ID: Application client IDMICROSOFT_CLIENT_SECRET: Application client secretMICROSOFT_TENANT_ID: Application tenant IDMICROSOFT_REDIRECT_URL: Application redirect URLhttps://api.<qalita-domain>/api/v1/auth/saml/callbackMICROSOFT_SCOPES:openid profile email https://graph.microsoft.com/User.Read
To create an application in Azure Active Directory (Azure AD) and configure SAML authentication for your platform, follow these steps to set up Single Sign-On (SSO) for your application using Azure AD as the identity provider.
1. Access the Azure Portal
- Log in to the Azure Portal with your administrator account.
2. Navigate to Azure Active Directory
- In the Azure Portal sidebar menu, select "Azure Active Directory" to access your Azure AD directory.
3. Register a New Application
- Go to the "App registrations" section.
- Click "New registration" to start creating a new application.
- Name your application, select the supported account types, and specify the redirect URL (callback) used after OIDC authentication. This URL should match
MICROSOFT_REDIRECT_URLyou will configure later in your environment variables.
4. Verify Authorized APIs
- Once the application is created, access it in the Azure Portal.
- In the application menu, find the "API permissions" section.
- Click "Add a permission" > "Microsoft Graph" > "Delegated permissions" > search for
User.Readand [Add permission].
5. Create an Application Secret
- Go to the "Certificates & secrets" section of your application.
- Click "New client secret" to create a new application secret. You will need this secret to configure Microsoft (OIDC) authentication in your platform.
- Use the value to configure the environment variable
MICROSOFT_CLIENT_SECRET.
6. Retrieve Application Details
- After configuring OIDC, retrieve the following information for your environment variables:
- Client ID (
MICROSOFT_CLIENT_ID): Found in the application's "Overview" section. - Client Secret (
MICROSOFT_CLIENT_SECRET): Create a secret in the "Certificates & secrets" section. - Tenant ID (
MICROSOFT_TENANT_ID): Visible in your Azure Active Directory "Overview".
- Client ID (
7. Configure Environment Variables
- On your server or development environment, configure the environment variables you retrieved in the previous step.
8. Test SAML Authentication
- Test SAML authentication to ensure everything is correctly configured and users can log in to your application via Azure AD.
By following these steps, you will have created an application in Azure AD, configured SAML authentication, and prepared your platform to use Azure AD as the identity provider for SSO authentication.
Note: The backend automatically exposes Microsoft/Google buttons on /signin when config is present (/api/v1/info).
JWT Token Authentication
Users can authenticate with an API token (for the backend), they have backend endpoint access relative to their user role.
To get your JWT API Token, you first need to authenticate to the platform, then go to your [Profile] page and then to the API Token section.
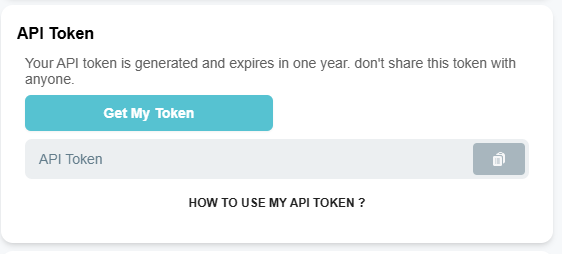
User API Token
Roles
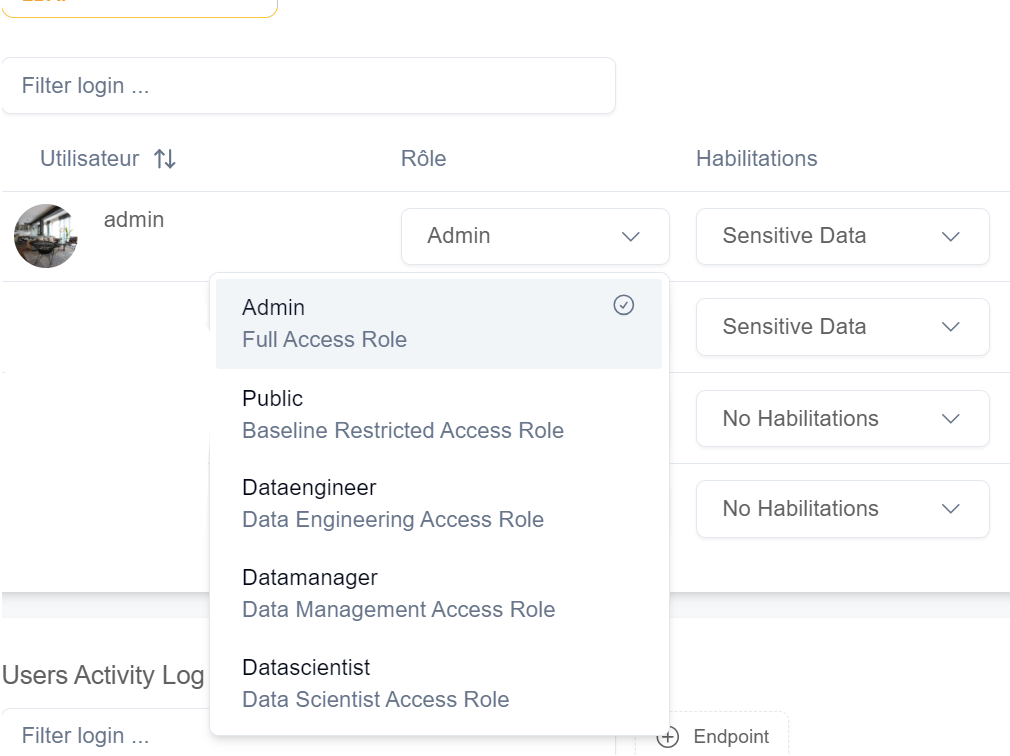
There are different roles in QALITA Platform that allow discrimination of possible actions and access rights.
| Role | Description | Permissions |
|---|---|---|
| Admin | The administrator role gives access to all platform features. | All |
| Dataengineer | The data engineer role has access to most platform features, except settings and data science. | Agents - Packs - Sources - Projects - Reports - Issues - Catalog |
| Datamanager | The data manager role has access to project, report, and ticket features. | Sources - Projects - Reports - Issues - Catalog |
| Datascientist | The data scientist role has access to catalog, report, and data science features. | Reports only with token - Catalog - Synthetic Data - Model Evaluation |
| Public | The public role has minimal access to platform features. | Profile - Notifications - Reports only with token |
Permissions
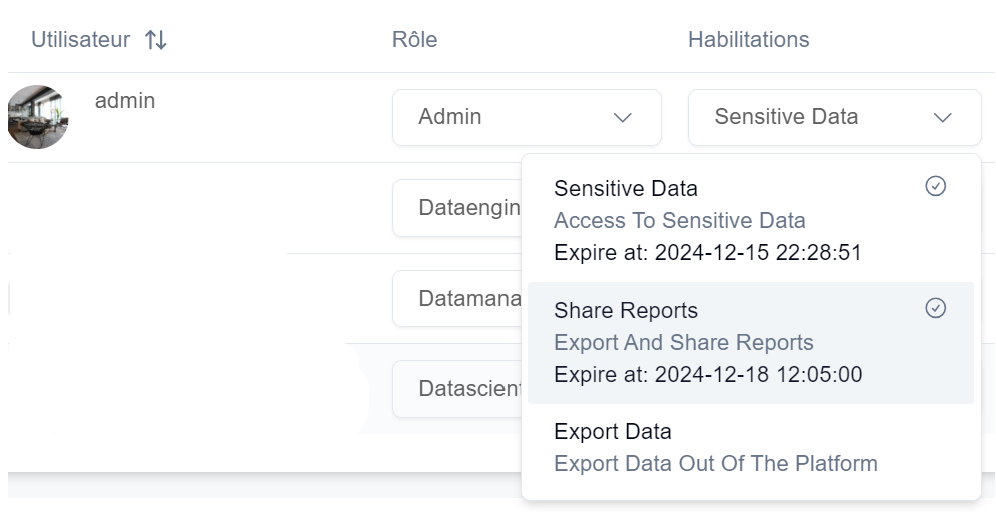
There are different permissions in QALITA Platform that allow granting rights for specific actions.
All permissions have a default lifetime of 1 year. They can be revoked at any time by simply clicking again on the permission in the user's permission list.
| Permission | Description | Authorizations |
|---|---|---|
| Sensitive Data | The Sensitive Data permission allows access to sensitive data. | Sensitive Data |
| Share report | The Share report permission allows sharing reports. | Report Sharing |
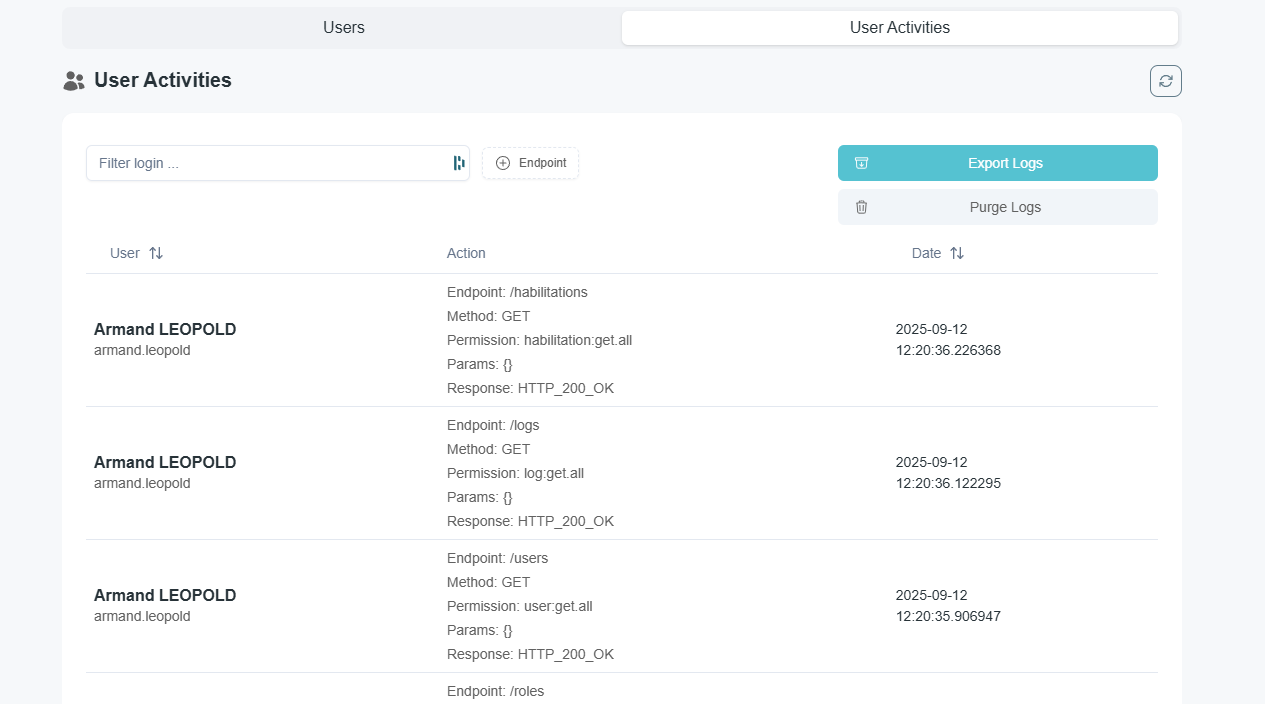
User Logs
Any actions made by any user is recorded in the logs table on the backend database.
User with admin roles can check latest logs and export them directly from the platform at [Settings] > [Users & Roles] > [Users Activities]
To know more about security, see the Security & Compliance page.